39+ SAMPLE Vulnerability Assessments
-

Vulnerability Assessment Policy
download now -

Database Vulnerability Assessment
download now -

Community-Based Vulnerability Assessment
download now -

Vulnerability Assessment and Management Policy
download now -

Security Vulnerability Assessment Template
download now -

Healthcare Hazard Vulnerability Assessment
download now -

Vulnerability Assessment in PDF
download now -

Vulnerability Assessment for Climate Adaptation
download now -
Vulnerability Assessment Worksheet
download now -

Vulnerability and Risk Assessment
download now -

Power Sector Vulnerability Assessment
download now -
Vulnerability Assessment Instrument
download now -
Socioeconomic Vulnerability Assessment
download now -

Airport Security Vulnerability Assessment
download now -

Vulnerability Assessment Framework
download now -

Cyber Security Vulnerability Assessment
download now -

Standard Vulnerability Assessment
download now -

Basic Vulnerability Assessment
download now -

Climate Vulnerability and Risk Assessment
download now -
Climate Change Vulnerability Assessment for Species
download now -

Coastal Flood Vulnerability Assessment
download now -

Security Vulnerability Self Assessment
download now -

Formal Vulnerability Assessment
download now -
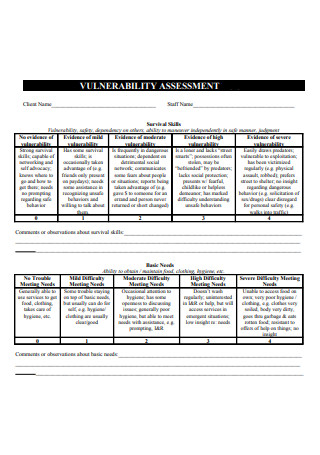
Vulnerability Assessment Example
download now -

Climate and Health Vulnerability Assessment
download now -

Governmental Vulnerability Assessment and Management
download now -

Joint Vulnerability Assessment
download now -
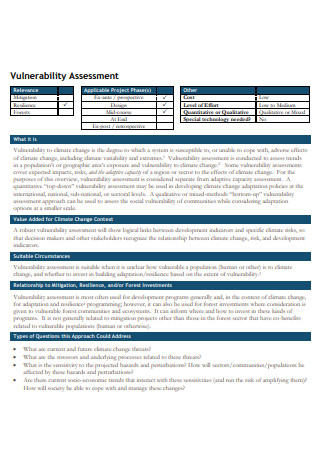
Vulnerability Assessment Format
download now -
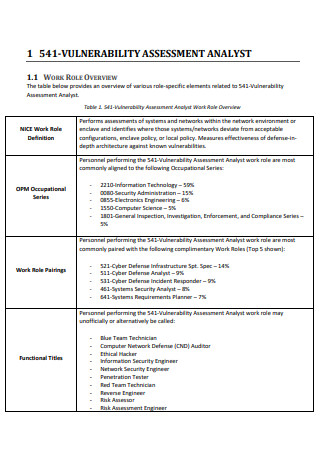
Vulnerability Assessment Analyst
download now -

External Network Vulnerability Assessment
download now -
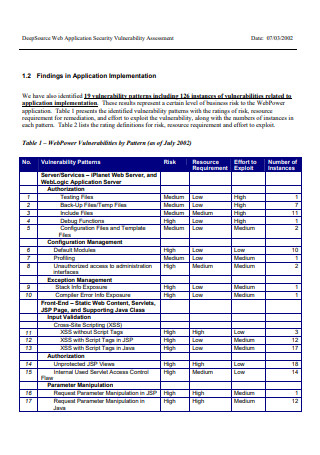
Web Application Security Vulnerability Assessment
download now -
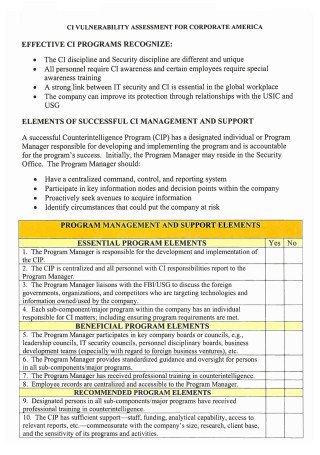
Corporate Vulnerability Assessment
download now -

Vulnerability Assessment with Application Security
download now -

Comprehensive Vulnerability Assessment
download now -

Sample Vulnerability Assessment
download now -

Event Tracker Vulnerability Assessment Service
download now -

Household Vulnerability Assessment
download now -

Vulnerability Assessment with Application Security
download now -

Facility Vulnerability Assessment Template
download now -

Liquid Fuels Vulnerability Assessment
download now
FREE Vulnerability Assessment s to Download
39+ SAMPLE Vulnerability Assessments
What Is a Vulnerability Assessment?
Types of Vulnerability Assessments
Types of Threats Prevented By Vulnerability Assessments
How the Vulnerability Assessment Process Works
FAQs
Why do we do vulnerability assessments?
What is VAPT?
What is OVAL in cyber security?
With the wide range of possibilities technology brings, there are issues with security that you can prevent with high-tech programs, devices, and processes. One of the several methods that businesses focus on to ensure the protection of their information systems is vulnerability assessment. What is a vulnerability assessment, and what makes it a vital tool for companies to incorporate into their technology endeavors? Learn more about a vulnerability assessment, including its description, structure, and creation, by reading the article below. The section also answers frequently asked questions about vulnerability assessments.
What Is a Vulnerability Assessment?
A vulnerability assessment is a process or systematic review of identifying, defining, classifying, and prioritizing vulnerabilities and weaknesses within an information system, including computer systems, applications, digital assets, and network infrastructure. The assessment evaluates the business’ systems for any susceptibility to vulnerabilities, estimates severity levels, recommends possible alleviating measures through remediation or remission when possible. The process of vulnerability assessments relies on vulnerability scanners to assess the systems. Businesses using this type of assessment must conduct scans regularly to guarantee that security networks, including adding new devices, installing additional equipment, or using new ports, are secure. Each evaluation provides information on potential vulnerabilities depending on the environment, new insights on risk levels, and possible mitigation strategies involving the vulnerabilities.
Companies ensure that their systems have mitigation capabilities when facing vulnerabilities. According to available data from Statista regarding IT vulnerability assessment marketing revenue worldwide from 2015-2016, the market predicts a generated revenue value of more than 1.7 billion US dollars. It means that organizations are willing to invest extensively in their systems’ security, spending thousands of dollars to guarantee that their information systems operate and perform properly.
Types of Vulnerability Assessments
Many organizations rely on technology to increase their communication capabilities with consumers. At the same time, technology ensures that their systems possess increased protection from any external threats. Vulnerability assessments help pinpoint vulnerabilities across different systems in the organization. Below are the types of vulnerability assessments according to the type of asset they can scan.
Types of Threats Prevented By Vulnerability Assessments
After identifying possible vulnerabilities through various types of vulnerability assessments, its job is to put up safety plans and prevent threats from accessing systems. Below are some examples of the hazards that vulnerability assessments determine and avert in an organization’s technological setup.
How the Vulnerability Assessment Process Works
A vulnerability assessment is a five-step process effectively ensuring the reliability of security systems across the company with an efficient application by professionals. The entire process is critical to vulnerability management and IT Risk Management lifecycles, becoming more effective with daily execution. Below are the steps in vulnerability assessments.
-
Step 1: Vulnerability Identification
The first step in vulnerability is identifying possible vulnerabilities of a system while creating a comprehensive list of each discovered vulnerability. Discovering the vulnerabilities requires a combination of vulnerability scanning and penetration testing. Vulnerability scanning is either authenticated or unauthenticated scans. Authenticated scans provide access to low-level data and allow scanners to access networks using remote administrative protocols, authenticating actions using system credentials. Meanwhile, unauthenticated scans do not have access to networks. It is the type of scan that attackers and security analysts use to determine third-party vendors or data leaks. Penetration testing can pinpoint security flaws and attack vectors unnoticed by vulnerability scanners run by a security team. Pen testing can also test security controls to see if they follow policies and protocols.
-
Step 2: Vulnerability Analysis
Upon identifying vulnerabilities, specify the components and the root causes responsible for these vulnerabilities. An example of a Root Cause for a vulnerability is an outdated version of an open-source library. Remediation is as easy as updating the library. However, it is not always the case for different problems. There are instances when organizations manually and individually run vulnerabilities to classify severity levels and specify effective solutions, whether to remediate or mitigate according to the risk management policies.
-
Step 3: Risk Assessment
The main objective of Risk Assessments is to prioritize the vulnerabilities. During this step, classification of severity levels occurs with the help of vulnerability assessment tools. Ensure that the assessment tool the company utilizes hasCommon Vulnerability Scoring System (CVSS). It assigns a numerical value to the severity of the vulnerability, ranging from 0 to 10. The vulnerability assessment report must include information about affected systems, sensitive data in systems, business functions, plan of compromise or attack, the severity of impact, accessibility, length of vulnerability, cost of a breach, and finally, organization regulatory requirements to make it effective.
-
Step 4: Vulnerability Remediation
The remediation process plans on fixing identified vulnerabilities and security issues that are unacceptable by the risk assessment. Remediation involves multiple teams working together, including development, risk management, compliance, operations, and security teams for Cost-Effective Analysis and remediation for different vulnerabilities. Various vulnerability management systems recommend typical remediation methods for known vulnerabilities, ranging from installing updates to replacing hardware. Particular remediation steps vary depending on encountered system vulnerabilities, including updating operating procedures, developing configuration management methods, and patching software.
-
Step 5: Vulnerability Mitigation
Since not all identified vulnerabilities can undergo remediation, enforcing mitigation processes is the next course of action. Mitigation focuses on reducing the occurrence of a specific vulnerability or diminishing its negative effect on the system. Mitigation methods include introducing new security measures, replacing wares, encryptions, attack surface management, vendor risk management, and persistent security monitoring.
FAQs
Why do we do vulnerability assessments?
Vulnerability scans are not sufficient in preventing attacks and protecting systems. There are various advantages to conducting vulnerability assessments with security providers with the right tools and techniques for pinpointing these vulnerabilities. Vulnerability assessments detect security vulnerabilities before any attackers. Companies will have a comprehensive inventory of devices with their purpose, along with their vulnerabilities. It also helps prepare businesses for planned subsequent upgrades. The testing also helps collect security reports for future assessments. Through the process, companies possess a well-defined risk assessment for their networks and prepare for hazards by optimizing security systems.
What is VAPT?
Vulnerability Assessment and Penetration Training or VAPT refers to a broad range of security assessment processes. The goal is to identify and address cyber security issues and exposures of the IT systems of an organization.
What is OVAL in cyber security?
OVAL stands for Open Vulnerability Assessment Language. It refers to an international information security community standard that offers publicly available security measures and content. OVAL consists of a language that encodes system details, including system repositories within the community.
No matter the size of your organization, when attackers attempt to attack information systems, they choose no one. Once these groups or individuals see an opportunity to infiltrate your technological structure, they will do it. It is best to put up precautions, especially when information systems of companies contain classified information about the company and its clients. Take the opportunity to perform vulnerability assessments for your organization regularly. Use the vulnerability assessment samples in PDF format, available in the article above. It’s better to be safe from any threats inside and outside the business than to resolve issues.
