28+ Sample Incident Management Plan
-

Incident Management Plan Template
download now -

Health System Incident Management Plan
download now -

Incident Management Planning Example
download now -

Standard Incident Management Plan
download now -

Critical Incident Management Plan
download now -
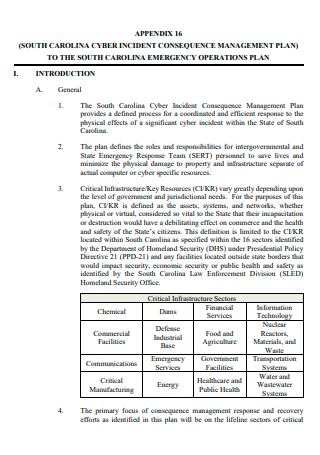
Cyber Incident Consequence Management Plan
download now -

Incident Management Plan Implementation
download now -

Simple Incident Management Plan
download now -

Major Incident Management Plan
download now -

Traffic Incident Management Plan For Work Zones
download now -

School of Art Incident Management Plan
download now -

Incident Management Plan in PDF
download now -
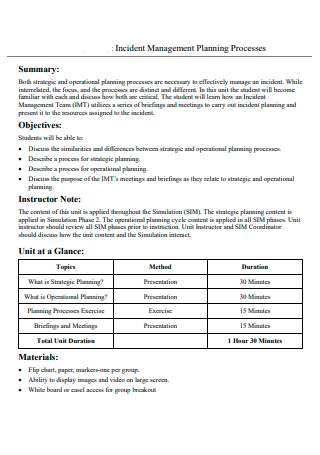
Incident Management Planning Processes
download now -

School Incident Management Plan
download now -

Pollution Incident Response Management Plan
download now -

Computer Incident Response and Management Plan
download now -

Multi-Casualty Incident Management Plan
download now -
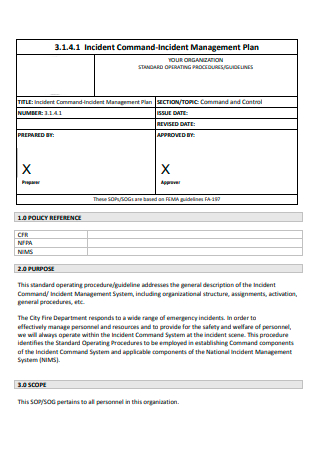
Incident Command Management Plan
download now -

Formal Incident Management Plan
download now -

Draft Incident Management Planning
download now -

College Incident Management Plan
download now -

Unclassified Incident Management Plan
download now -

Sample Incident Management Plan
download now -

Incident Management Plan For Medicines
download now -
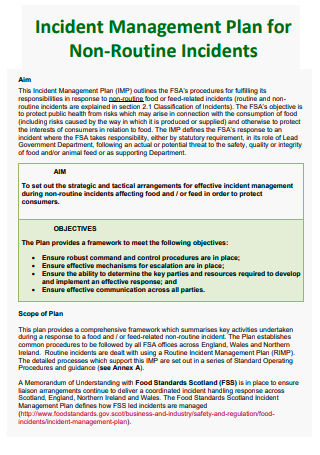
Non-Routine Incident Management Plan
download now -

Incident Response Emergency Management Planning
download now -

Printable Incident Management Plan
download now -
Company Incident Management Plan
download now -

Incident Management Plan in DOC
download now
FREE Incident Management Plan s to Download
28+ Sample Incident Management Plan
What Is an Incident Management Plan?
Components of an Incident Management Plan
How to Develop an Incident Management Plan
FAQs
What are the five stages of the incident management process?
What is the KPI for incident management?
What is an IR plan?
What Is an Incident Management Plan?
An incident management plan is also known as an incident response plan or emergency management plan. It is a business document that aids an organization to return to its normal operations as soon as possible, following an unforeseen event. The incident management plan also recognizes possible weaknesses in the system, mitigates the impact of various situations, and limits the effect on the reputation, operations, and financial capacity of the organization. With the increase in several security issues at present, including ransomware attacks and data breaches, organizations must ensure they have a system to mitigate and recover from these situations. Instead of waiting for these occurrences to happen, companies must be proactive and secure an incident management plan. The plan serves as a break or make point of the company when it comes to response effectiveness. Incident management can also be part of a larger planning document like the overall business continuity management plan. Services restoration depends on the impact and severity of the event with temporary solutions. Generally, the use of the incident management plan focuses on recognizing an incident, assessing a situation, notifying affected individuals or departments, organizing and mobilizing response techniques and resources, and documenting the recovery process.
According to the information from Securelist entitled Incident Response Analyst Report 2019, victims of incidents show that less than a quarter of received requests are false positives, mostly suspicious files or activities in systems. True positive requests include the discovery of suspicious and encrypted files and alerts from security tools. Most incidents happen in the Middle East at 32.6 percent, the European Union at 24 percent, and the Commonwealth of Independent States at 21.7 percent.
Components of an Incident Management Plan
An incident management plan is a vital document in ensuring that a company can function after an unforeseeable event. The contents of the plan must communicate the necessary responses the organization must perform to make sure that operations can continue as soon as possible. Below are the essential elements that the incident management plan must contain.
How to Develop an Incident Management Plan
In terms of cyber security, the goal of the incident management plan is to address detected data breaches using different phases. In each phase of the plan, the members of the incident management team must consider and perform to find possible solutions. Below are the phases to follow when developing the incident management plan.
-
1. Preparation Phase
The initial step to the incident management plan serves as the workhorse and the most crucial phase to protect the business. During the preparation phase, the organization ensures that all the employees have the proper training and knowledge about their roles and responsibilities in the event of a security breach. There must also be a development of incident response drills and possible scenarios, including the regular conduction of mock data breaches for evaluation. In the preparation phase, the organization also approves necessary budget plans for the implementation of the plan. The management plan must be well-documented, highlighting personnel duties and testing performance, to guarantee the best response.
-
2. Identification Phase
In the identification phase, the incident management team determines whether there is an event of security or data breach, and it can originate from different areas. In this step, the team members must identify the time of occurrence, method of discovery, the person responsible, impacted areas, the scope of the compromise, operational implications, and the point of entry.
-
3. Containment Phase
At the initial discovery of a breach, the initial response is to delete it. However, it will affect the company in the long run for destroying valuable evidence to determine the source of the breach, and from there, develop a plan to prevent its reoccurrence. Contain the breach to prevent its spread to different systems and cause further damage to the organization. Try disconnecting devices from the internet, and prepare to perform short-term or long-term containment strategies. Setting up system backups also helps with restoring business operations. It is advantageous to perform system updates and patches, scan remote access protocols, modify user and administrative access credentials, and strengthen password lists.
-
4. Eradication Phase
After the containment process, the next step is to detect and destroy the root cause of the breach. As a result, begin securely removing all malware, patch and harden all systems, and apply the necessary updates. The company has the option of hiring a third-party specialist to perform the steps thoroughly. If there are malware or security issues that remain in the systems, there is still the risk of losing data, decreasing liabilities.
-
5. Recovery Phase
In this step, responsible personnel takes the time to restore and return affected systems and devices and incorporate them back to business operations. At this time, take the necessary steps to get the company running once again without the fear of running into another breach. It is also advisable to keep monitoring systems and devices and prepare the necessary tools to counter any reoccurrence of attacks.
-
6. Lessons Learned
After the overall incident investigation, hold a post-incident meeting with the incident management team members and discuss all necessary information and learnings from the event. This step allows the company to analyze and record details about the breach. The team then determines the processes and techniques that were successful and indicates any possible holes in the system. This step helps strengthen the future responses to future attacks.
FAQs
What are the five stages of the incident management process?
The five steps of incident resolution include incident identification and categorization, incident notification and escalation, incident diagnosis and investigation, resolution and recovery, and closure.
What is the KPI for incident management?
Key performance indicators are measurement tools that aids organizations to determine whether they are reaching their business goals. In terms of incident management, the necessary metrics that must be present include the number of incidents, resolution time, and the average time between each incident.
What is an IR plan?
An IR plan or an incident response plan is more common terminology for the incident management plan. It details pre-determined instructions and processes to detect, respond to, and limit possible data breaches in organizational systems.
Every organization must ensure the safety of its resources, especially those that are within systems. It is better to be proactive than reactive when it comes to handling security breaches in the business. As early as possible, prepare possible mitigation methods and processes to help the organization at the possibility of unforeseen events. Design your incident management plan by downloading the samples available in the article, and ensure that your company is ready for any incident that comes your way.
