5+ Sample Information Security Proposal
-

Information Security Center Budget Proposal
download now -
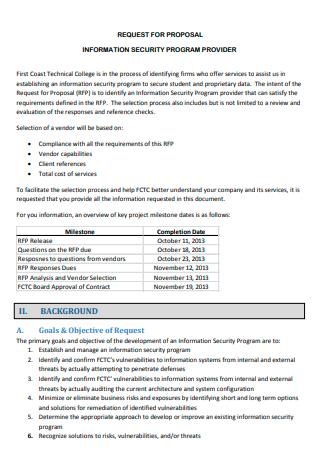
Information Security Program Provider Proposal
download now -

Information Security Third Party Proposal
download now -

Information Security Strategy Proposal
download now -

Network and Information Security Proposal
download now -
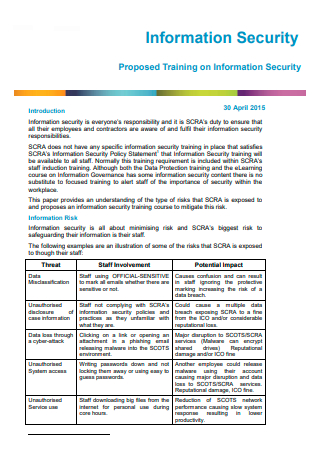
Information Security Proposal in PDF
download now
FREE Information Security Proposal s to Download
5+ Sample Information Security Proposal
What Is Information Security?
Who Manages Information Security?
What Are Information Security Threats?
How Does Information Security Fit in With Information Risk Management?
How Do You Respond to Information Security Threats?
What Are the Benefits of an Information Security Proposal?
Key Principles of Information Security
How to Write an Information Security Proposal
FAQs
Who is responsible for the security report?
Do a security proposal and a security report differ?
What is a good cybersecurity strategy?
What Is Information Security?
Generally, information security is concerned with preventing unwanted access to information. It is a component of information risk management and entails preventing or lowering the likelihood of illegal access, use, disclosure, disruption, deletion, corruption, alteration, inspection, or recording of information systems and data. It is the responsibility of information security experts to mitigate the negative consequences of a security event if it does occur. It is important to note that information can be either electronic or physical, tangible or immaterial. However, while sustaining organizational productivity is typically an important factor when developing an information security program, the primary objective of any information security program should be protecting the confidentiality, integrity, and availability (the CIA triad) of information.
Other templates are available on our website, and you can use them whenever you need them. They are as follows: security services proposal, buyout agreement, security audit, Labor Contract, cyber security proposal, staffing agreement, business lease proposal, security management proposal, property purchase agreement, construction bid proposal, security bid proposal, and other similar templates are available. This post will not only provide you with templates but will also provide you with important information that you need to know in order to complete your template.
Who Manages Information Security?
Natural disasters, server failures, physical thievery, and unpatched endpoints are all examples of threats to information security. While paper-based businesses continue to exist, the growing reliance on information technology has elevated information security to a critical component of cyber security risk management, necessitating the hiring of dedicated IT security specialists. These data security, application security, network security, computer security, physical security, and data loss prevention experts are concerned with data security, application security, network security, computer security, physical security, and data loss prevention.
Recognize that data, applications, and computers are extending far beyond the boundaries of what is usually considered a computer. Smartphones, tablets, and other mobile devices are every bit as much of a computer as a server or mainframe and are vulnerable to hostile cyber assaults that can result in the disclosure of sensitive information, important information, or information assets. IT chief security officer (CSO), chief information security officer (CISO), security engineer, information security analyst, security systems administrator, and IT security consultant are all common professions that demand experience in information management.
What Are Information Security Threats?
A variety of threats exist, including software attacks, identity theft, sabotage, physical theft, and information extortion, amongst others.
- Viruses, malware, worms, ransomware such as WannaCry, trojan horses, and other dangerous codes that interfere with the availability of information are examples of software attacks against information security systems.
- Phishing emails and websites are frequently used to steal intellectual property or log-in credentials in order to obtain unauthorized access to a system. Social engineering is one of the most serious cyber risks today, and it is difficult to defend against with typical security methods.
- Sabotage attempts, such as denial of service assaults, frequently try to decrease the availability of critical information assets, so diminishing confidence and organizational productivity until money is made in exchange for the organization’s service being restored.
- Theft of information and equipment is becoming increasingly widespread as more and more items, such as smartphones and laptops, become mobile in their nature and thus easier to steal. The cloud is becoming more and more reliant on security than at any other time in history.
Information extortion is the illegal practice of acquiring access to confidential information and holding it hostage until a ransom is paid.
How Does Information Security Fit in With Information Risk Management?
When it comes to information risk management, it is the process of identifying vulnerabilities and threats to information resources used by an organization and determining what, if any, countermeasures should be implemented in order to reduce risk to an acceptable level based on the importance of the information to the organization. When it comes to risk management processes, there are two major considerations:
1. Risk Management as an Ongoing Process
In order to be effective, risk management must be an ongoing and iterative process that must be performed endlessly as new risks and vulnerabilities arise.
2. Balance in Countermeasures
A balance must be struck between productivity, cost, efficacy, and the information value of the asset that is being protected when selecting countermeasures or controls.
How Do You Respond to Information Security Threats?
When a threat is recognized, you have a choice between two options:
- Decrease or mitigate the risk by putting in place safeguards or countermeasures that will eliminate or reduce risks and vulnerabilities as much as possible.
- Risk can be transferred to another entity or organization by obtaining insurance or contracting with a third party.
- Accept the risk when the cost of the countermeasure is greater than the potential cost of loss as a result of a vulnerability or a cyber assault, for example.
What Are the Benefits of an Information Security Proposal?
A proposal for information security is a document that contains thorough information regarding security procedures or measures that are necessary to address risks and potential dangers in the information technology environment. Security businesses write them and use them to coordinate with clients that hire them in order to develop an effective security service system for their clients.
1. Increase Your Awareness of Potential Risks
In recent years, businesses have grown their reliance on cloud computing technology and other technologies such as mobile devices, the Internet of Things (IoT), and wearables, among other things, increasing their vulnerability to cyber threats and assaults. Consequently, companies must be more tactical in their defenses than they have ever been before to be safe. Before you can begin to mitigate risks, however, you must first gain a thorough understanding of the threat landscape, as well as your own weaknesses and deficiencies. The ability to detect threats in their early phases is also advantageous. Your organization will benefit from receiving a comprehensive overview of your current information technology environment, which will allow you to make the necessary security improvements.
2. Proactive Security Should be Enabled
One of the key reasons organizations become targets of cybercrime is the fact that they are reactive in their operations. Keeping a false sense of security and taking proactive actions to improve your cybersecurity are crucial to avoid. Rather than waiting for an attack and then responding to it, it is preferable to have IT support specialists monitor and maintain systems on a constant basis. Regardless of the environment, organizations should always be prepared for the worst-case scenario. Proactive approaches such as penetration testing, security vulnerability scanning, business continuity planning, and managed security are just a few examples of what may be done to protect an organization.
3. Responds in a Timely Manner
As previously said, no organization, even those with the most stringent security procedures in place, is completely safe from attack. Even the most sophisticated defenses can be breached by specific attacks that are tailored to the situation. Because of this, having a cyber security policy in place could be beneficial. A successful cyber-attack requires the development of specific processes for mitigating the harm to the greatest extent feasible, and creating this plan is a necessary part of that process. Each employee will be aware of their individual responsibilities in responding to the crisis, thereby avoiding stress, upheaval, and misunderstandings among colleagues.
Key Principles of Information Security
Security of information is fundamentally based on the three principles of confidentiality, integrity and availability (sometimes known as the CIA triad). There is some controversy as to whether or not the CIA trinity adequately addresses quickly changing technological and business requirements, as well as the interplay between security and privacy, among other things. Other principles, such as responsibility, have been presented, and non-repudiation does not appear to be a good fit with the three fundamental notions.
How to Write an Information Security Proposal
Following your understanding of information security best practices and completion of a Risk Assessment of your organization’s information security structure, you will be prepared to begin designing your information security roadmap. What is the best way to develop an information security strategy?
-
Step 1: Describe the Situation
In order for your client to be aware of the existing situation, The reality is that if they do not require security services, they will not seek them out on their own. To learn more about your client’s problem, conduct research, and interviews with them. This will serve as a guideline for how to formulate the security proposal, which will be based on the planning that occurs around it.
-
Step 2: Create a Positive Public Image
To dispel any feelings of informality, portray the proper picture of your firm by stating how long you have been in business and never forgetting to mention the notable clientele who have benefited from your services. This will increase people’s confidence in your company’s security services and their willingness to accept the contents of your proposal.
-
Step 3: Provide the Most Effective Solution
This is the meat of your security plan, and it should be read carefully. Once the problem has been identified, you should propose the solution that you believe will be the most effective in combating it. Example: If the issue is the presence of a large group of VIPs at an event, write about the need for event security in the venue to guarantee that everyone feels safe.
-
Step 4: Make a Plan for Your Content
Once you’ve gathered all of your information for your proposal, adopt a format that will make it easier to organize it all. Make certain that it contributes to your reader’s comprehension of everything in the letter. To learn more about security, you might look at checklists and security statements.
Every business must safeguard itself against Cyber Attacks and security dangers. Cybercrime and malware are a constant threat to anyone with an Internet connection, and data breaches are time-consuming and costly. The services of a reputable information security supplier will help mitigate digital information dangers and ensure that systems continue to operate normally. Not all businesses demand the same level of data protection. You must find a provider with whom you can operate on a daily basis and who can meet your business’s needs. A strong partnership with a security services provider results in increased productivity, fewer disruptions, and a better reputation for your firm.
FAQs
Who is responsible for the security report?
The security company’s front office normally creates and finalizes the security proposal. They know more about security than anyone else.
Do a security proposal and a security report differ?
While both include security, they differ in that they are planned ahead of time. Afterwards, a security report is written.
What is a good cybersecurity strategy?
A cybersecurity strategy outlines how a company will secure its assets and reduce cyber risk. Like a cybersecurity policy, a cybersecurity strategy should evolve with the threat landscape and the company environment.
Computer system and physical data security is intended to protect the confidentiality, integrity, and availability of computer system and physical data from unauthorized access, whether or not the access is malevolent in nature. The CIA triad refers to the three characteristics of confidentiality, integrity, and availability. Protection of the CIA trinity while sustaining organizational productivity is at the heart of every information security effort, and this is no exception.
