Security Incident Report Samples
-

Annual Security Incident Report
download now -

Network Security Incident Report
download now -

Ledger Security Incident Report
download now -

IT Security Incident Report
download now -

Security Incident Report Template
download now -

Construction Security Incident Report Template
download now -

Simple Security Incident Report Template
download now -

Security Guard Incident Report Template
download now -

Security Guard Incident Response Report
download now -
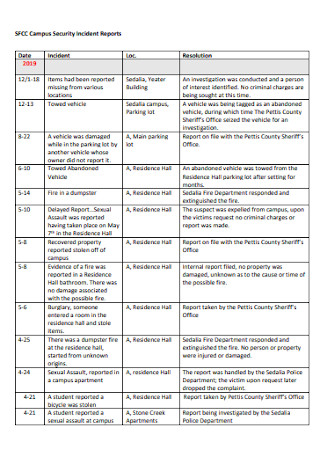
Hospital Security Incident Report
download now -

Blank Security Incident Report
download now -

Information Technology Cyber Security Incident Report
download now -
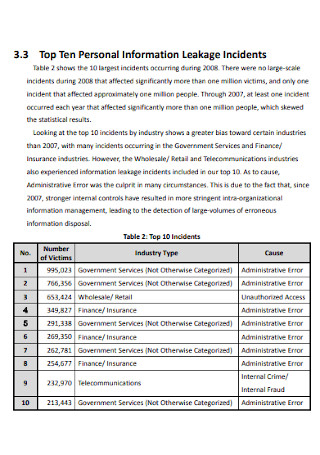
Security Incident Survey Detailed Report
download now -

Monthly Report of Security Incident
download now -
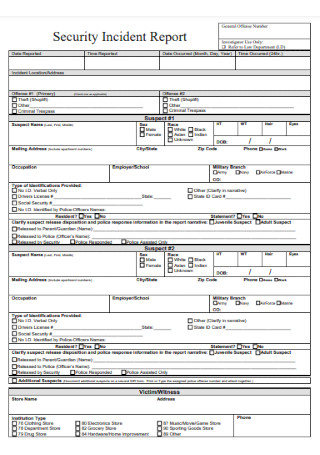
Short Security Incident Report
download now -

Safety Security Incident Report
download now -

Security Data Incident Response Report Form
download now -

Data Breach Security Incident Report
download now -

Security Officer Incident Report
download now -

Sample Security Incident Reporting Form
download now -

Test Security Incident Report
download now -
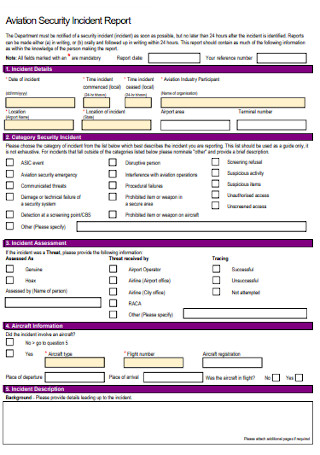
Aviation Security Incident Report
download now -

Judicary Security Incident Report
download now -

Basic Security Incident Report
download now -

Security Incident Policy Report
download now -

Privacy Security Incident Report
download now -

Information Security Incident Report
download now -
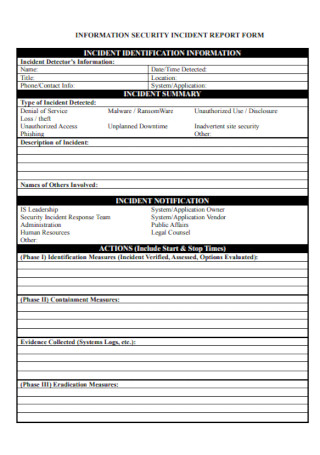
Security Information Incident Report
download now -
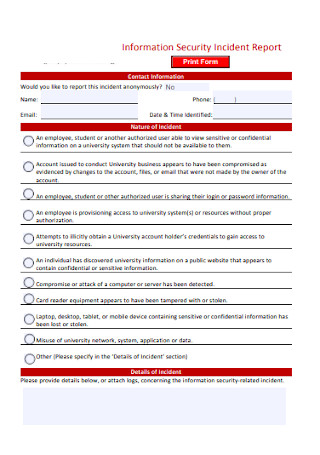
Sample Security Incident Report
download now -
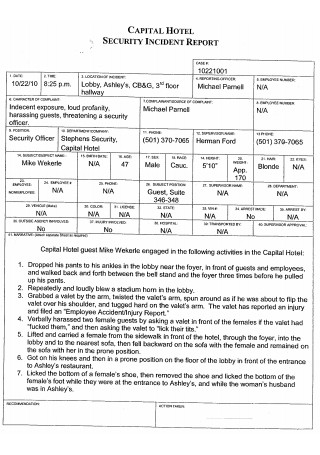
Hotel Security Incident Report
download now -
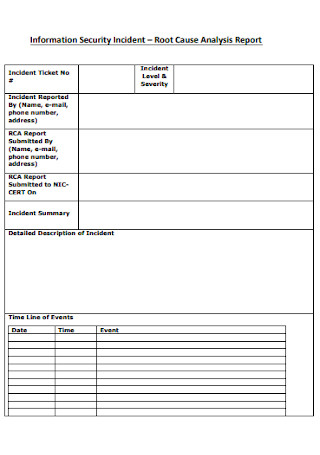
Security Incident Analysis Report
download now -
Security Incident Investigation Report
download now -

Simple Information Security Incident Report
download now
FREE Security Incident Report s to Download
Security Incident Report Format
Security Incident Report Samples
What is a Security Incident Report?
What is Included in a Security Incident Report?
How to Properly Write a Security Incident Report
FAQs
Why should someone make a Security Incident Report?
Should any incident be reported, even if it is a very small one?
What happens to a security incident report after it has been filed, and investigation is concluded?
How often should Security Incident Reports be updated?
What are the key components of a Security Incident Report?
How do Security Incident Reports aid in compliance?
What challenges are common in creating Security Incident Reports?

Download Security Incident Report Bundle
Security Incident Report Format
Report Details
- Report Number: [Unique ID]
- Report Date: [Date]
- Reported By: [Name and Title]
- Contact Information: [Phone Number, Email Address]
Incident Summary
- Date and Time of Incident: [Date, Time]
- Location of Incident: [Specific Location]
- Type of Incident: [Physical Security Breach, Cybersecurity Breach, Unauthorized Access, etc.]
- Affected Parties/Entities: [Employees, Systems, Third Parties, etc.]
Incident Description
[Provide a detailed account of the incident. Include specifics about what occurred, how it was discovered, and any initial actions taken.]
Immediate Actions Taken
- [Action 1: Brief Description]
- [Action 2: Brief Description]
- [Action 3: Brief Description]
Impact Assessment
- Assets Affected: [Description of compromised data, equipment, systems, or personnel]
- Severity Level: [Low, Medium, High, Critical]
- Potential Consequences: [Business disruption, data loss, legal implications, etc.]
Investigation Details
- Investigating Officer/Team: [Name(s) and Title(s)]
- Investigation Start Date: [Date]
- Investigation End Date: [Date]
- Key Findings:
- [Finding 1: Description]
- [Finding 2: Description]
- [Finding 3: Description]
Root Cause Analysis
[Provide an explanation of the root cause of the incident, including contributing factors.]
Corrective and Preventive Actions
- Corrective Actions:
- [Action 1: Brief Description]
- [Action 2: Brief Description]
- Preventive Measures:
- [Measure 1: Brief Description]
- [Measure 2: Brief Description]
Witness Information (If Applicable)
- Witness Name: [Name]
- Contact Information: [Phone Number, Email Address]
- Statement: [Attach detailed witness statement if necessary]
Supporting Evidence
- [List and attach logs, photos, videos, or other relevant documents.]
Sign-Offs
- Prepared By: [Name and Signature]
- Reviewed By: [Name and Signature]
- Approval: [Name and Title]
What is a Security Incident Report?
A Security Incident Report is an essential document that is used to keep track of any untoward security incidents that occur in a workplace or an organization, such as theft, vandalism, etc. It is a detailed report of the events leading up to the incident that took place. Reporting these security incidents is a crucial part of letting the workplace manage and prepare on dealing with such incidents should they ever occur again, as it ensures that all security incidents are tracked, captured, and dealt with by the workplace or organization. Should they fail to track such incidents, they won’t be able to manage it. You can also see more on Security Incident Response Reports.
What is Included in a Security Incident Report?

The contents of a Security incident report are usually different from one workplace or organization to another. You can also see more on Preliminary Incident Report. Here are the most common contents that are included in a security incident report:
How to Properly Write a Security Incident Report

Writing a Security Incident Report can be a daunting task to perform for some people, especially if this is their first time writing one. It can also be the least favorite part for those people who are working in the security sector. Being guided by the instructions written in the incident report can be a massive help for them. If not, then hopefully these steps can help:
1. Gather as much information as possible.
Ask as many people as you can who saw the incident happening for details. Then gather all the necessary data, such as the date, time, and location of said incident. If they give you permission, also include the names, the departments, and contact details of the people you’ve interviewed during the information gathering. Including their contact details enables the authorities to contact them should they have any further questions or developments regarding the incident that took place.You can also see more on Hotel Incident Report.
2. Fill up your personal details.
As you begin writing on the report, it is also important to write your personal information in the spaces provided, including your name, contact details, your company details, and your home address. This enables the investigators to know who wrote the security incident report, and also enables them to contact you for further information, or to ask for clarification should they find any inconsistencies in your report.
3. Write what actually happened.
This is where you write the events that actually took place. But you should remember to stick to the facts of the incidents, and never, ever include your own opinions. You should only write the facts that you are 100% sure it took place. You can also write down all the information that you have gathered from the people you’ve asked from. Also remember to use as little technical jargon as possible, for your report to be easily understood by the investigators. You should also format the report properly, and avoid writing a very long paragraph so that your report is easier to read. You can also include here a timeline of how the security incident occurred. In writing the incident, you can remember the 5 Ws (What, Where, Why, Who, When) and 1 H (How) to make the report more authentic and credible. You can also see more on Audit Incident Reports.
4. Verify and proofread.
Once you’ve completed writing the security incident report, it is important to double-check what you’ve actually written in your report for missing information and facts, for story inconsistencies, and for grammatical errors. Make sure that all the events that you’ve written match what actually happened, and all the facts, names, and dates that you’ve listed down are factual. This is your opportunity to polish your written report because any unseen typographical error can be detrimental to the progress of the investigation and may change its outcome.
5. Submit the report to the authorities.
Once you’ve double-checked the security incident report you’ve written, and you’re confident that everything in the report is true and correct, it is now time to submit your report to the investigator or to the authorities, so they can begin their investigation and provide their appropriate recommendation report and feedback. Be sure to have your lines ready in case they contact you during the investigation period.
FAQs
Why should someone make a Security Incident Report?
Creating a security incident report enables us to create an external account of the incident that occurred, which can be of great help to the legal proceedings that will follow. Having such an incident reporting system in place also helps the organization or the company to enforce its own security policy. By also developing a reporting culture in the workplace, the chances of a simple incident transforming into a full security event also get reduced greatly. You can also see more on Information Security Reports.
Should any incident be reported, even if it is a very small one?
Yes, security incidents of all types must be reported and tracked. It is important to do so because reporting incidents is an essential part of a workplace’s security management program. These reports are stored and are eventually used as evidential documentation to serve as proof that the workplace regulations and standards are properly complied with by the workplace. Employees should also be frequently reminded of the security incident reporting process, no matter how small the incident may be.
What happens to a security incident report after it has been filed, and investigation is concluded?
In most cases, a summary of every security incident report that has been filed within a certain period of time is compiled on a yearly basis. Sometimes, it is also compiled every 6 months. The summary is usually distributed among the members of the company’s senior management team. You can also see more Hospital Incident Report.
How often should Security Incident Reports be updated?
Reports should be updated as new information becomes available during the investigation or resolution process.
What are the key components of a Security Incident Report?
A Security Incident Report includes the date, time, and location of the incident, the systems or data affected, the root cause, response actions, and lessons learned. These details ensure comprehensive documentation and aid in preventing similar incidents. You can also see more on Job Incident Report.
How do Security Incident Reports aid in compliance?
Many industries require detailed incident reporting to meet legal and regulatory standards. Accurate Security Incident Reports help demonstrate due diligence and adherence to these requirements, reducing potential penalties.
What challenges are common in creating Security Incident Reports?
Challenges include incomplete data collection, lack of standardized templates, miscommunication among teams, and insufficient analysis of incident impact. Overcoming these requires thorough planning and clear communication. You can also see more on Incident Violation Report.
